We fully replace the provided key, as a private key portion should remain as private as possible, and should definitely have a passphrase! This is the skillset to enahnce your server with tools available to anyone.
We want our customers to know they could handle the task, but want us to fulfill the order right.
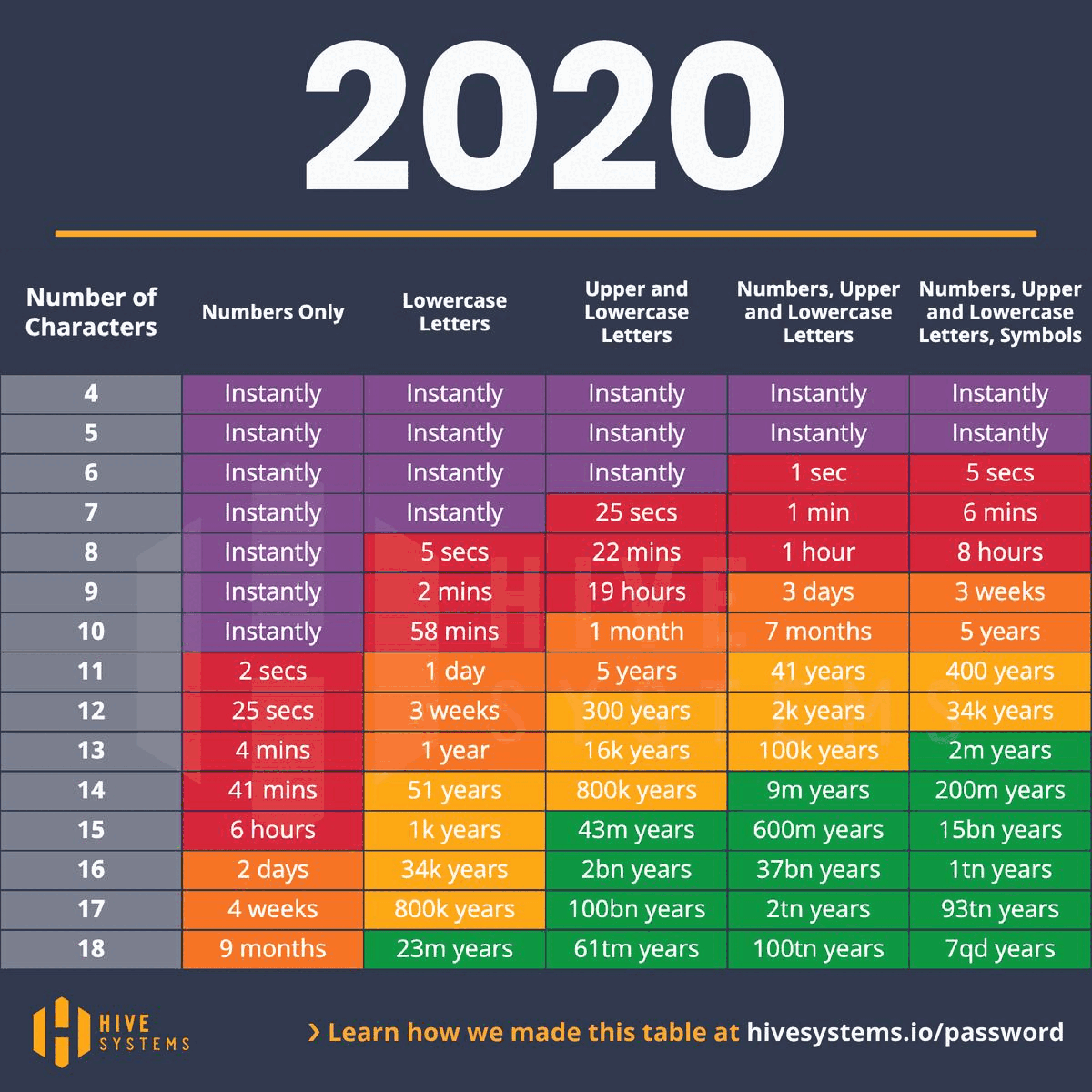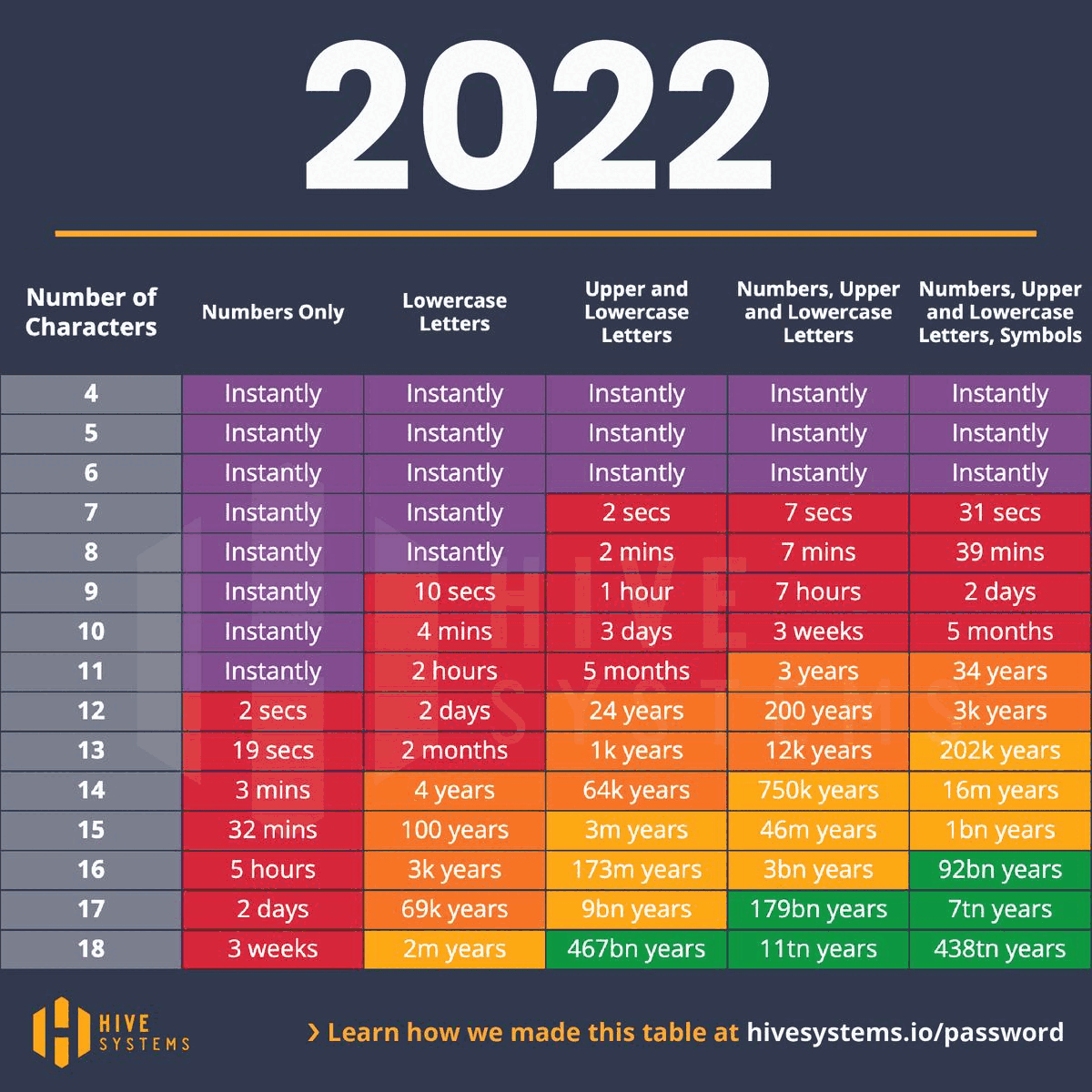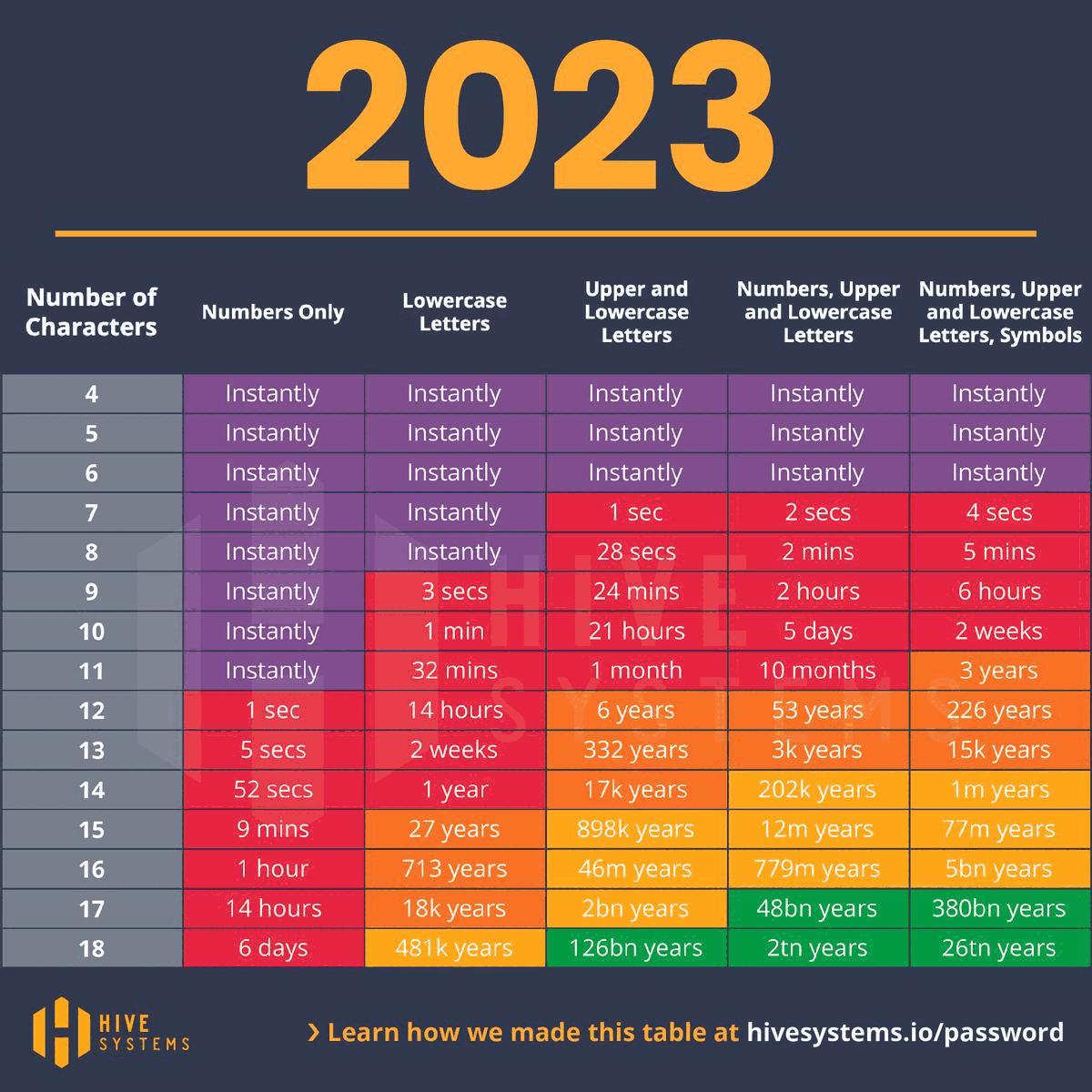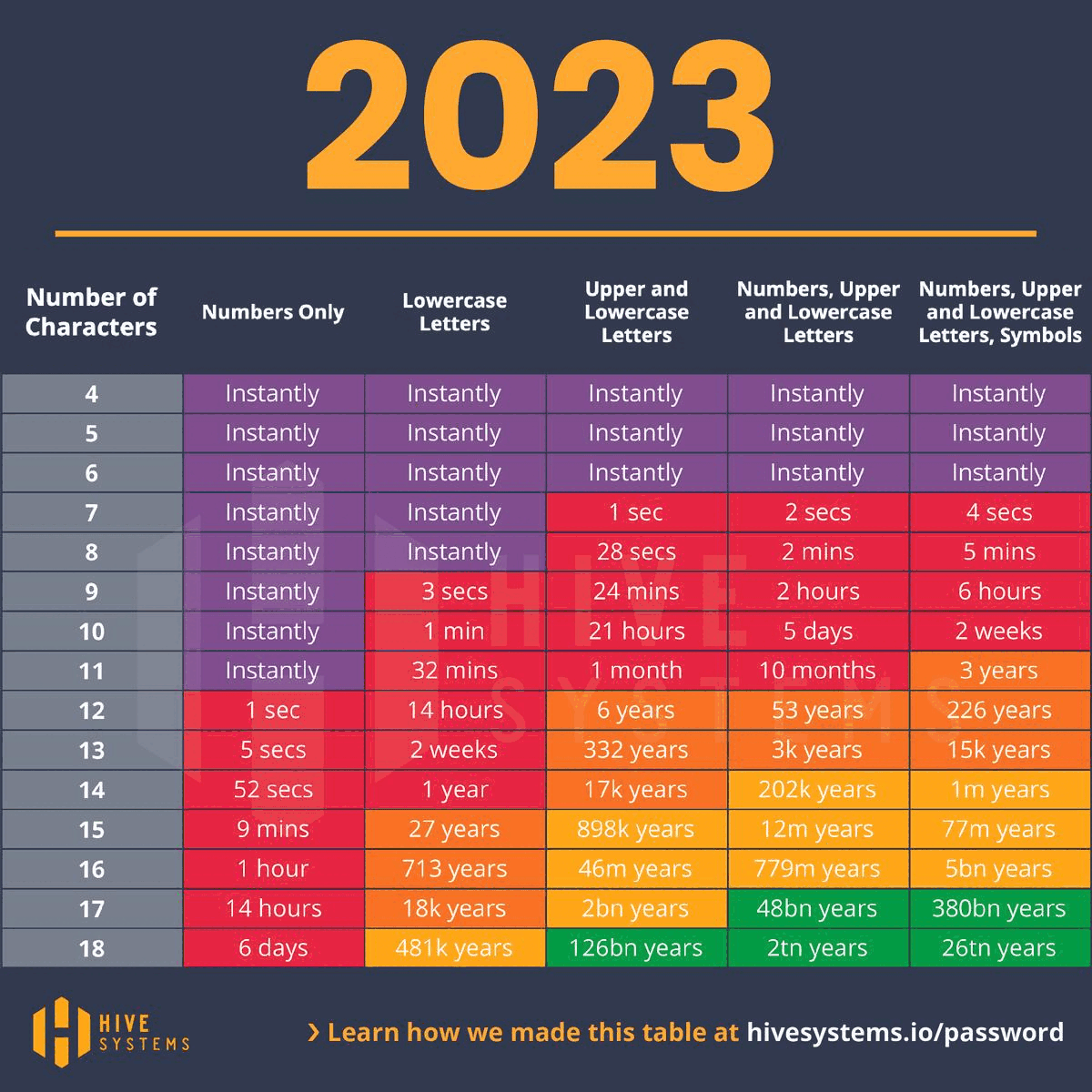
And as time goes on, everyone, bad guys included, are getting faster and faster...
[S]ecure [SH]ell:
Secure SHell encrypts the communication between the client and the server, ensuring that sensitive data, including login credentials and commands, cannot be easily intercepted or read by unauthorized parties. This encryption is crucial for maintaining the confidentiality and integrity of data during remote sessions.
The Linux shell is a command-line interface (cli) thatsectionows users to interact with the operating system by entering commands and receiving text in response. This serves as a method for you and I to have a conversation with the system, enabling the system to perform tasks like file manipulation, program execution, and system administration following our directions.
Authentication and Authorization:
SSH provides strong user authentication methods, such as password-based authentication and public key authentication. This ensures that only authorized users can access the server if they have the right keys to the locks.
Z\ cannot stress enough the necessity of a strong password along with good security hygeine. No one solution will fix everything, but 13+ character phrases with some creative $ymb0l$ are a strong start.
SSH authenticated servers allow us to define who can see what and what control which users or systems can connect to the server. This granular control helps protect servers from unauthorized access.
We solve this by recommending a debian-based system with a strong user password maintaining their secure design.
You're the only user with the keys once we're done.
What you do thereafter is YOUR choice! It's YOUR server, afterall!
Remote Command Execution/Admnistration:
SSH enables system us and developers to manage and administer servers remotely using the command-line interface. Itsectionows for tasks such as configuring settings, installing software, and troubleshooting issues without physical access to the server.
SSH can work with tools like scp (secure copy) and rsync that facilitate secure file transfers between local and remote systems. This is useful for uploading, downloading, and synchronizing files and directories.
In short, we're trying to provide you with the tools to assist in securing your data.
OR: How to summarize many lifetimes of work into s run-on sentance
Encryption is the process of using math to make it hard for anything that doesn't know what you started with to understand the information you handed off or needed to read.
I cannot do these people justice that have made it safe for us to buy online. Please read more about the realities of what it took to make encryption happen.
[External: Wikipedia]
Exactly, here's the basic steps to making and using a key with the ssh-keygen function downloadable in the Linux operating system.
Generate the SSH Key Pair: Open a terminal on your Linux or UNIX-based system.
Execute the command
to create a new ED25519 SSH key pair.
Specify File Location and Passphrase: You will be prompted to specify the file location to save the key.
Press Enter to accept the default location
Enter passphrase (empty for no passphrase):
When asked to enter a passphrase, type a secure passphrase of your choice.
This adds an extra layer of security to your SSH key.
You will be prompted to enter same passphrase again:Make sure you're taking your time typing, we can all switch 2 letters without noticing.
Check Generated Keys: After completing the above steps, two files will be generated in the specified directory, usually
.
The
file is your private key, and
is the public key... key is a terrible word, it's the lock.
This is what's put on the server and attackers have to get through.
will move you into the SSH folder of the current user.
will display your new lock to be put on your server.
Copy Public Key to Server: Mac and Windows Subsytem for Linux have a strong avantage here of being able to copy paste...
Just
Copy, and win.
For the rest of the world, you can use
transfer to the destination using your preferred method, then
(inside
) on your remote server. Remember, this is the public facing portion, anyone knocking at the door knows it's there.
Test SSH Connection: Now, try SSHing into your server. You'll be prompted to enter the passphrase you set earlier, and then you should be granted access.
to log in using the lock and key combination you just made!